Hacking Networks with Nmap (Education Purpose only)
🎯 Let’s Understand ️ ️
What is Nmap?
Why use Nmap?
Is Nmap safe to use?
Installing Nmap on Linux.
Scanning a Single Target.
Scanning Multiple Targets.
Scanning an IP Address Range.
Scanning an Entire Subnet.
Scan a Target List.
Scanning and Excluding Targets
Aggressive Scan.
✍️ What is Nmap?
Nmap (Network Mapper) is a free, open-source network exploration and security auditing tool. It is used to discover hosts and services on a computer network, thus creating a map of the network topology.
Nmap uses various techniques to scan a network, including ping sweeps, port scanning, version detection, and OS detection. It can also perform advanced functions like scriptable interaction with the target, fingerprinting, and vulnerability detection.
✍️ Why use Nmap?
Nmap is often used by network administrators to manage and secure their networks by identifying vulnerabilities that may be exploited by attackers. Security professionals can also use it to perform penetration testing, which involves attempting to exploit vulnerabilities in a network or system to identify potential security threats.
Nmap is a powerful tool that requires knowledge and skill to use effectively. It should only be used on networks that you have permission to scan and should be used with caution to avoid any unintended consequences.
Network Mapping:
Nmap can be used to discover hosts and services on a network, creating a map of the network topology. This can help network administrators to manage and secure their networks by identifying potential security risks and misconfigured devices.
Vulnerability Scanning:
Nmap can be used to identify vulnerabilities in hosts and services. By scanning for open ports and known vulnerabilities, Nmap can help security professionals to identify potential weaknesses in a system that could be exploited by attackers.
Penetration Testing:
Security professionals often use Nmap to perform penetration testing, which involves attempting to exploit vulnerabilities in a network or system to identify potential security threats.
System Auditing:
Nmap can be used to audit system configurations, including operating systems and network devices. This can help administrators to ensure that their systems are properly configured and that security policies are being enforced.
Troubleshooting:
Nmap can be used to troubleshoot network connectivity issues. By scanning for open ports and network services, Nmap can help identify issues with firewalls or misconfigured devices.
Nmap is a safe tool to use as long as it is used responsibly and ethically. When used without permission, Nmap can be used for malicious purposes such as hacking, network attacks, or information theft. However, when used with permission, Nmap is a valuable tool for network administrators and security professionals to identify vulnerabilities in their networks and systems.
✍️Is Nmap safe to use?
It’s important to note that some network devices or systems may consider Nmap scans as a form of attack or intrusion, and may trigger security alarms or block the scan. Therefore, it’s important to obtain permission from the owner of the network or system before running any Nmap scans. Additionally, it’s important to use Nmap’s various scanning options and features judiciously to avoid causing any damage to the target network or systems.
Overall, Nmap is a safe and powerful tool when used responsibly and ethically. It’s important to obtain permission, use caution, and respect the security and privacy of the target network or system when using Nmap.
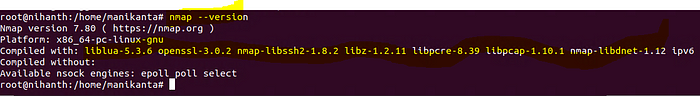
✍️ Installing Nmap on Linux?
sudo apt-get update && sudo apt-get update

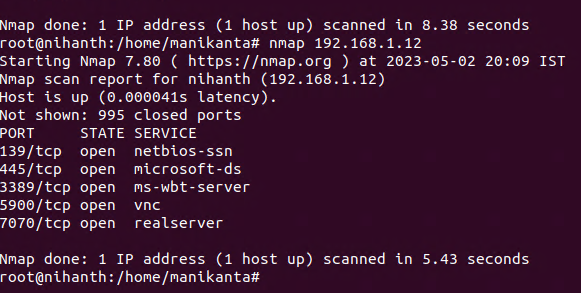
✍️ Scanning a Single Target?
Nmap 192.168.1.12
✍ ️Scanning Multiple Targets?
nmap [target1 IP or hostname] [target2 IP or hostname] [target3 IP or hostname] …

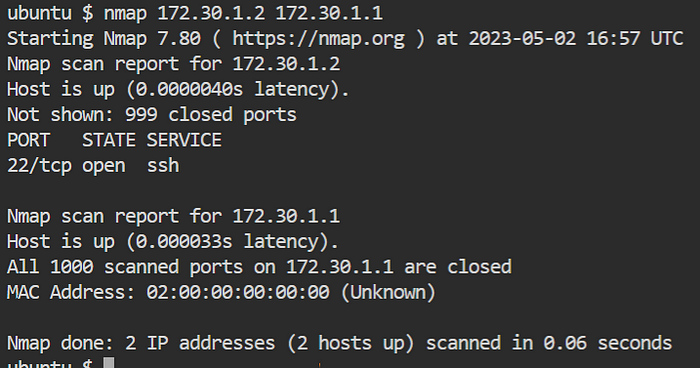
✍️Scanning Multiple Targets?
nmap 172.30.1.2 172.30.1.1
✍️Scanning an Entire Subnet?
nmap 172.30.1.2/24
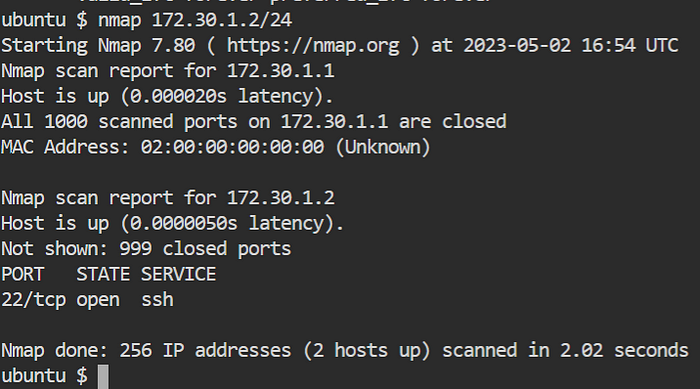
✍️Scanning an IP Address Range?
nmap 172.30.1.2–100
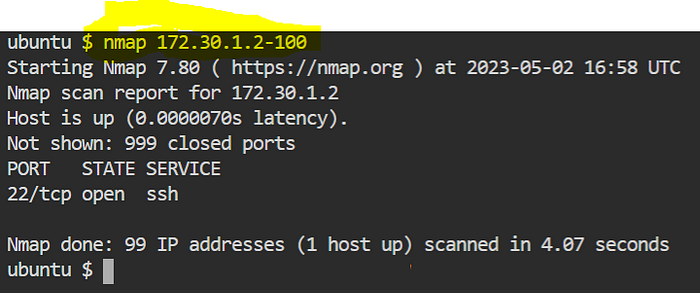
✍️Scan a Target List?

✍️Scanning and Excluding Targets?
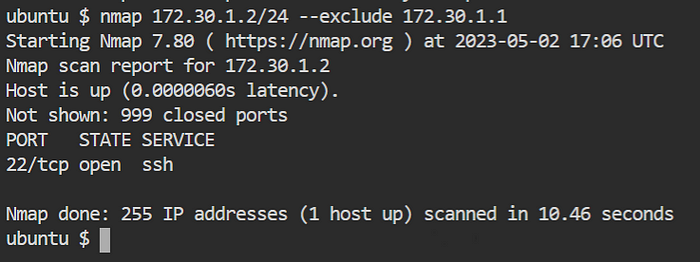
✍️Aggressive Scan?

